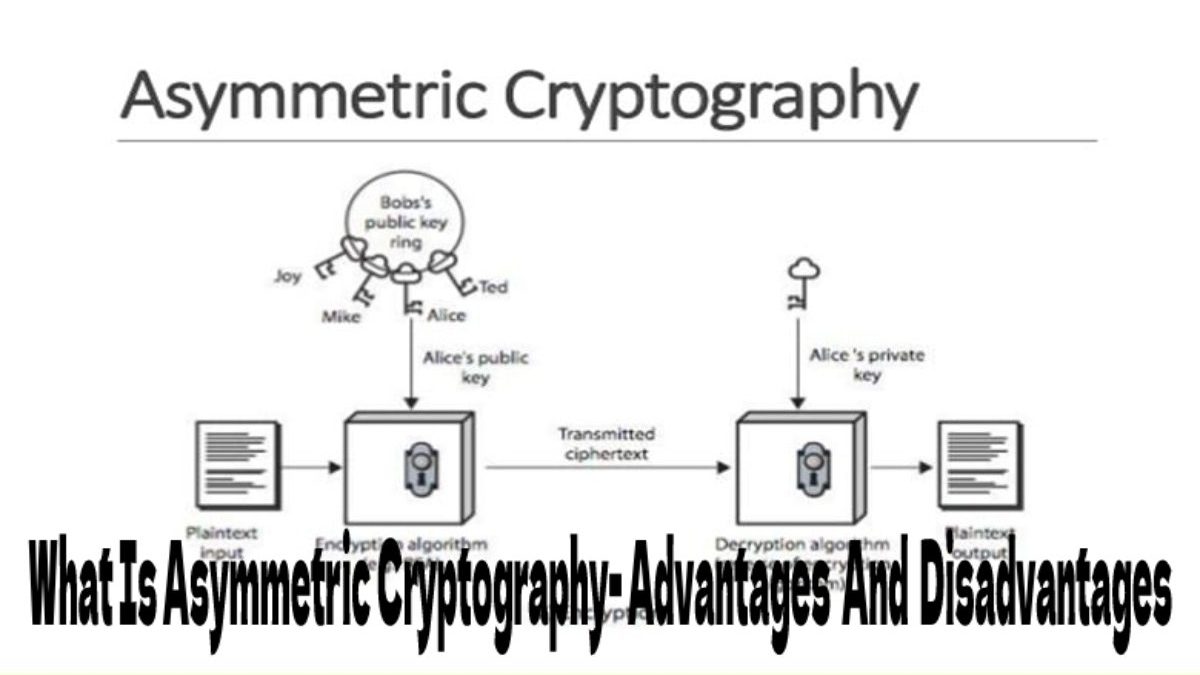
Asymmetric cryptography is one of the most potent computer encryption methods, based on a relatively sophisticated mathematical formula to generate a pair of keys: the private and public keys. Both the sender and the receiver must employ asymmetric cryptography with the same technique to develop a unique and unrepeatable set of keys for each other
The sender and receiver provide their public keys throughout this communication process, which will then use to encrypt the communications they transmit and receive. And the private keys will decode the contacts to see what they contain. This technique prevents a third party from interfering with the transmission or knowing the letter range.
This approach, which appears simple but conceals years of study and sophisticated algorithms, is widely utilized. May found asymmetric encryption in our WhatsApp or Telegram chats, as well as in our email access.
Table of Contents
Beginnings Of Asymmetric Cryptography
Asymmetric cryptography saw its birth in 1976, when Ralph Merkel, Whitfield Diffie, and Martin Hellman created the first public asymmetric cryptography system. Although not precisely asymmetric, the Diffie-Hellman algorithm was a crucial first step in developing this technique, which soon saw more contributions from other researchers.
It would be in 1977 when Ron Rivest, Adi Shamir, and Leonard Adleman created the RSA algorithm. This first public asymmetric cryptography algorithm would become an industry standard to this day, where the evolution of technology has allowed the further development of this encryption technique.
How Does Asymmetric Cryptography Work?
The operation of asymmetric encryption follows a series of steps that guarantee that the system is entirely secure and maintains the secrecy of the communications exchanged through it.
Select The Encryption Algorithm And Curve
The first step for asymmetric encryption to work is to choose the algorithm to use because each has unique properties. There are currently dozens of algorithms, some more secure than others depending on their complexity, but the most common are RSA, ECDSA, EdDSA, and ElGamal; each of these algorithms uses its mathematical system.
Also Read: Asset Tokenization – Definition, Concept, Characteristics, Advantages
Asymmetric Cryptography – Key Generation
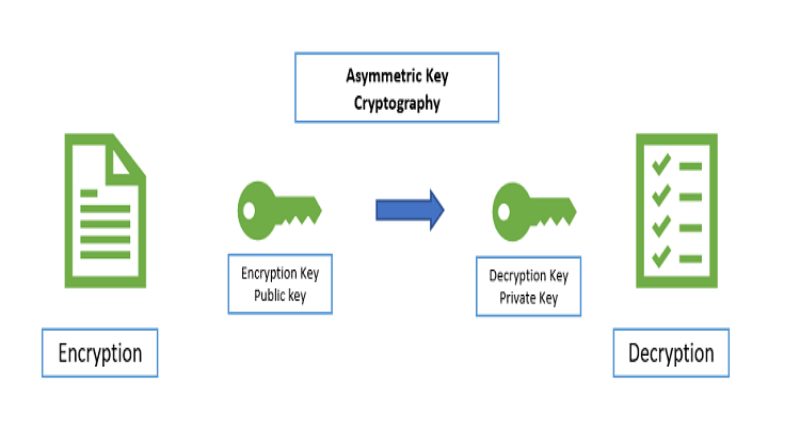
Once the algorithm has been decided, the next step is to generate the public and private keys.
The first key to being generated using this cryptography technique is the private key. We only have this key, and it arises as to the result of taking random data and transferring it to a mathematical problem. A considerable number is obtained after going through a conversion process
We can generate the public key through a complex mathematical process that relates the private key to a mathematical formulation with the private key. Again, it will transform a considerable number into a long string of numbers and letters as the public key.
Thus, the private key is an encryption seed, from which we can create as many public keys as we need. The private key also decrypts the messages we receive from the people we give our public keys. In addition, the private key allows us to digitally sign the letters. Thus confirming the authenticity of the communication since no one can duplicate the private key.
For its part, the purpose of the public key is that the people to whom we give it can encrypt the messages and send them to us. It is essential to point out that the public key allows messages to be encrypted. But the opposite process, decrypting them, is practically impossible. It is so because the private and public keys will relate to the algorithm used to create them. The public key also verifies the authenticity of the digital signatures that our messages carry.
Advantages and Disadvantages of Asymmetric Cryptography
Advantages
- It has a high-security rate since the encryption scheme is very complex; this makes cryptanalysis difficult and brute force attacks to break it useless.
- Thanks to public and private vital sets, it ensures open and public communication channels.
- It allows authenticating the information thanks to a digital signature system. For example, in the FNMT certificates, a system without encrypted critical repudiation will use
- They have a high level of confidentiality and integrity.
Disadvantages
- Compared to a symmetric cipher, it is computationally more expensive and slower.
- It is no stranger to external issues; for example, a faulty random number generator would compromise the entire encryption system.
- Given the complexity of the algorithms, detecting failures or bugs is more difficult in this type of system.
- Centralized trust propagation schemes can reduce vulnerability to certificate tampering if the structure will compromise.
Use Of Asymmetric Cryptography In The Blockchain
Blockchain technology has sought since its inception to offer the most significant possible security to its users. In that search, asymmetric cryptography has played an essential role since secure and private communications will ensure thanks to private and public keys.
In addition, blockchain technology has been the ideal testing ground for developing new cryptographic techniques that have not benefited all of computing, such as schemes such as Zero-Knowledge Proofs (ZKP) or Schorr signatures.
Also Read: Security Token Offering – Definition, How To Work, Benefits, And More


Review What Is Asymmetric Cryptography- Advantages And Disadvantages.